Protecting your business Simon Whittaker Cyber Security Director - Vertical Structure Ltd https://vsltd.co/ABNI2019
Slide 1
Slide 2
Prepare, Protect, Persist ® • Prepare • We help you and your partners to understand how to identify and resolve potential security issues at the earliest stages with hands on ‘hack yourself first’, threat modelling and GDPR compliance workshops as well as security training for non-technical colleagues. • Protect • Using automated and manual penetration testing techniques, we provide a comprehensive security report for your Web and mobile applications, including API testing, and networks. The report highlights potential issues and their resolutions. • Persist • We ensure that your organisation benefits from continual improvements in security levels through information assurance processes, auditing and certification including ISO27001:2013 and Cyber Essentials. © Vertical Structure Ltd where applicable [email protected]
Slide 3

http://www.visualcapitalist.com/internet-minute-2018/ © Vertical Structure Ltd where applicable [email protected]
Slide 4
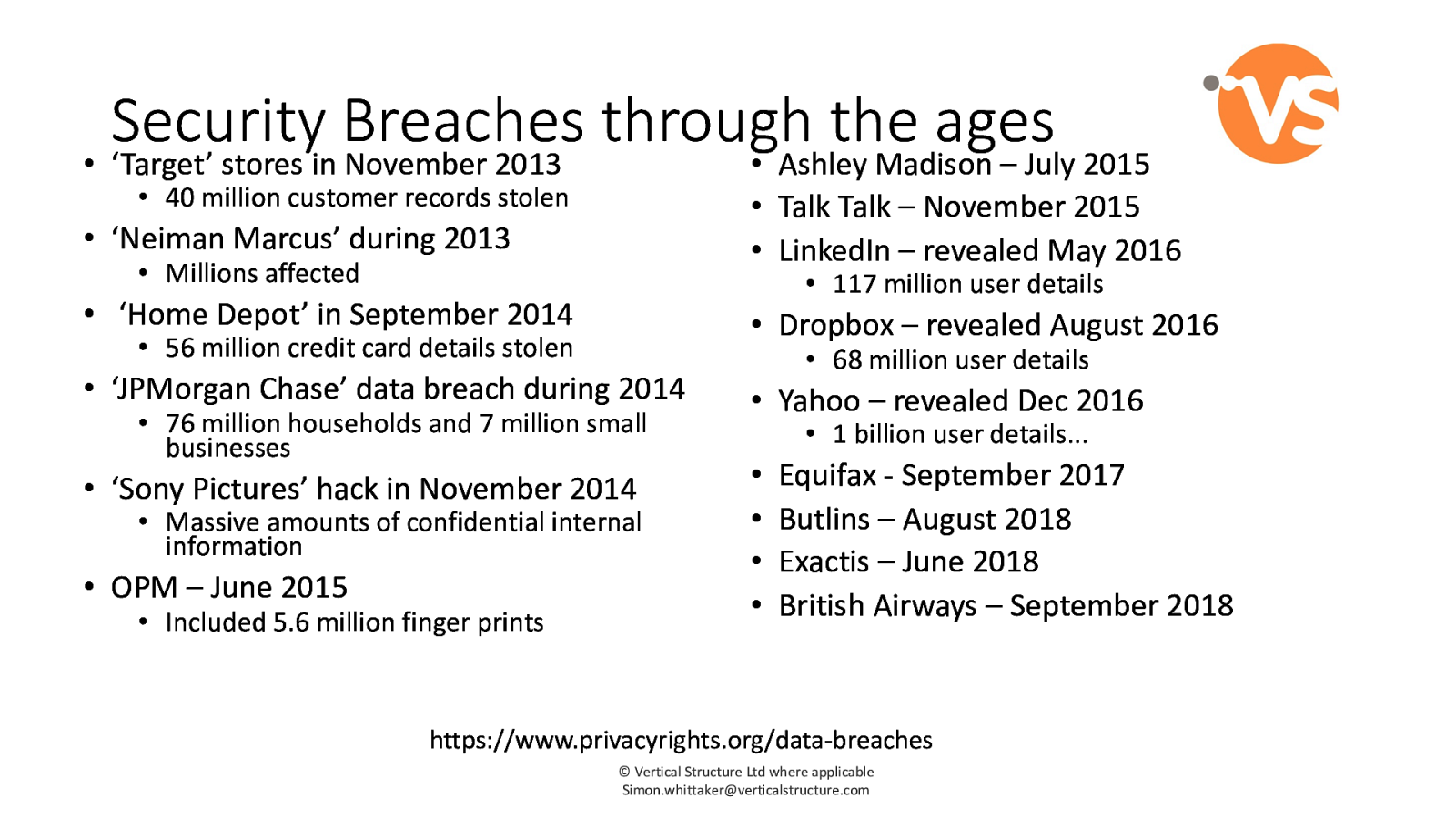
Security Breaches through the ages • ‘Target’ stores in November 2013 • Ashley Madison – July 2015 • 40 million customer records stolen • Talk Talk – November 2015 • LinkedIn – revealed May 2016 • ‘Neiman Marcus’ during 2013 • Millions affected • 117 million user details • ‘Home Depot’ in September 2014 • Dropbox – revealed August 2016 • 56 million credit card details stolen • ‘JPMorgan Chase’ data breach during 2014 • 76 million households and 7 million small businesses • ‘Sony Pictures’ hack in November 2014 • Massive amounts of confidential internal information • OPM – June 2015 • Included 5.6 million finger prints • 68 million user details • Yahoo – revealed Dec 2016 • 1 billion user details… • • • • Equifax - September 2017 Butlins – August 2018 Exactis – June 2018 British Airways – September 2018 https://www.privacyrights.org/data-breaches © Vertical Structure Ltd where applicable [email protected]
Slide 5
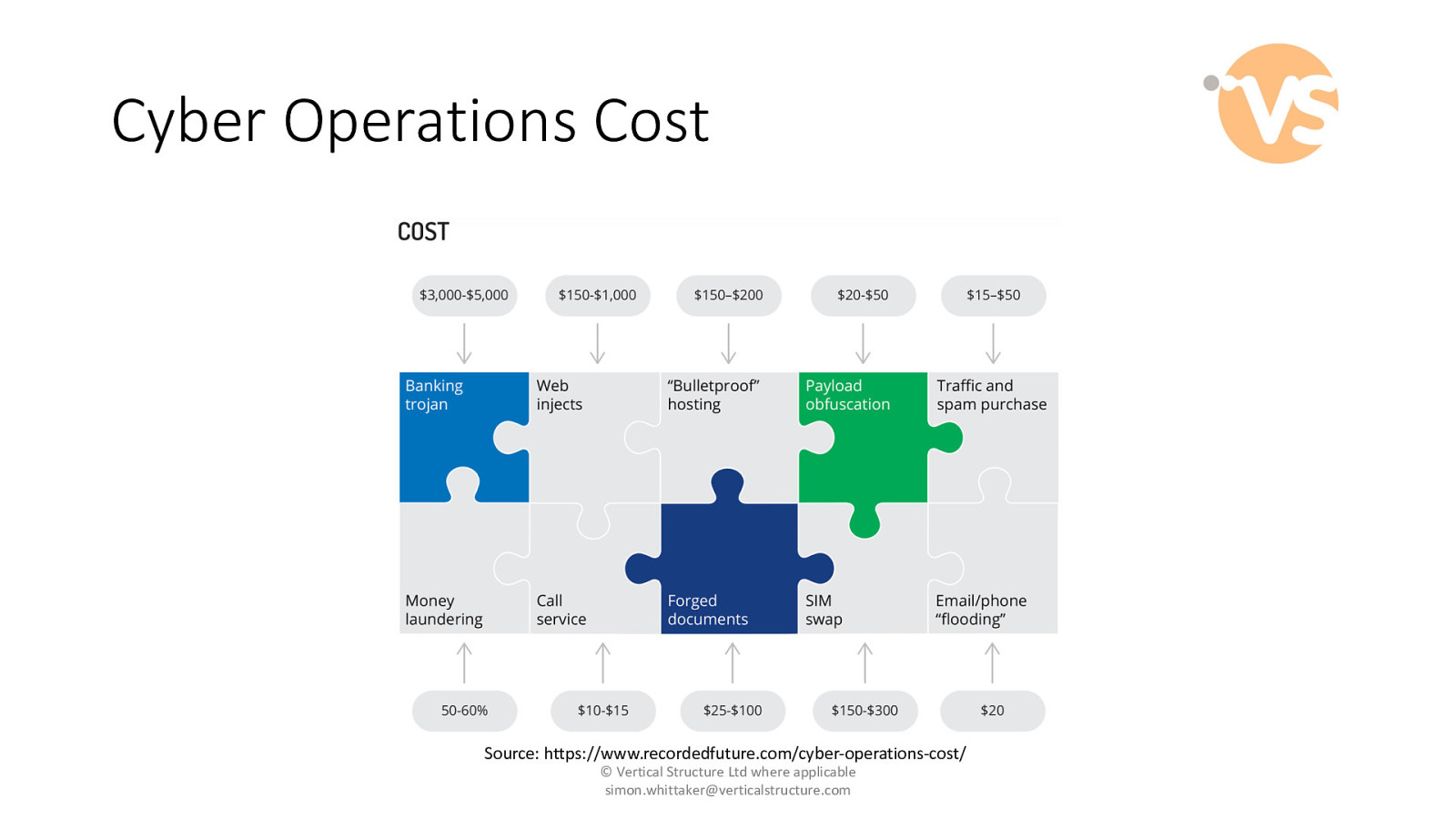
Cyber Operations Cost Source: https://www.recordedfuture.com/cyber-operations-cost/ © Vertical Structure Ltd where applicable [email protected]
Slide 6
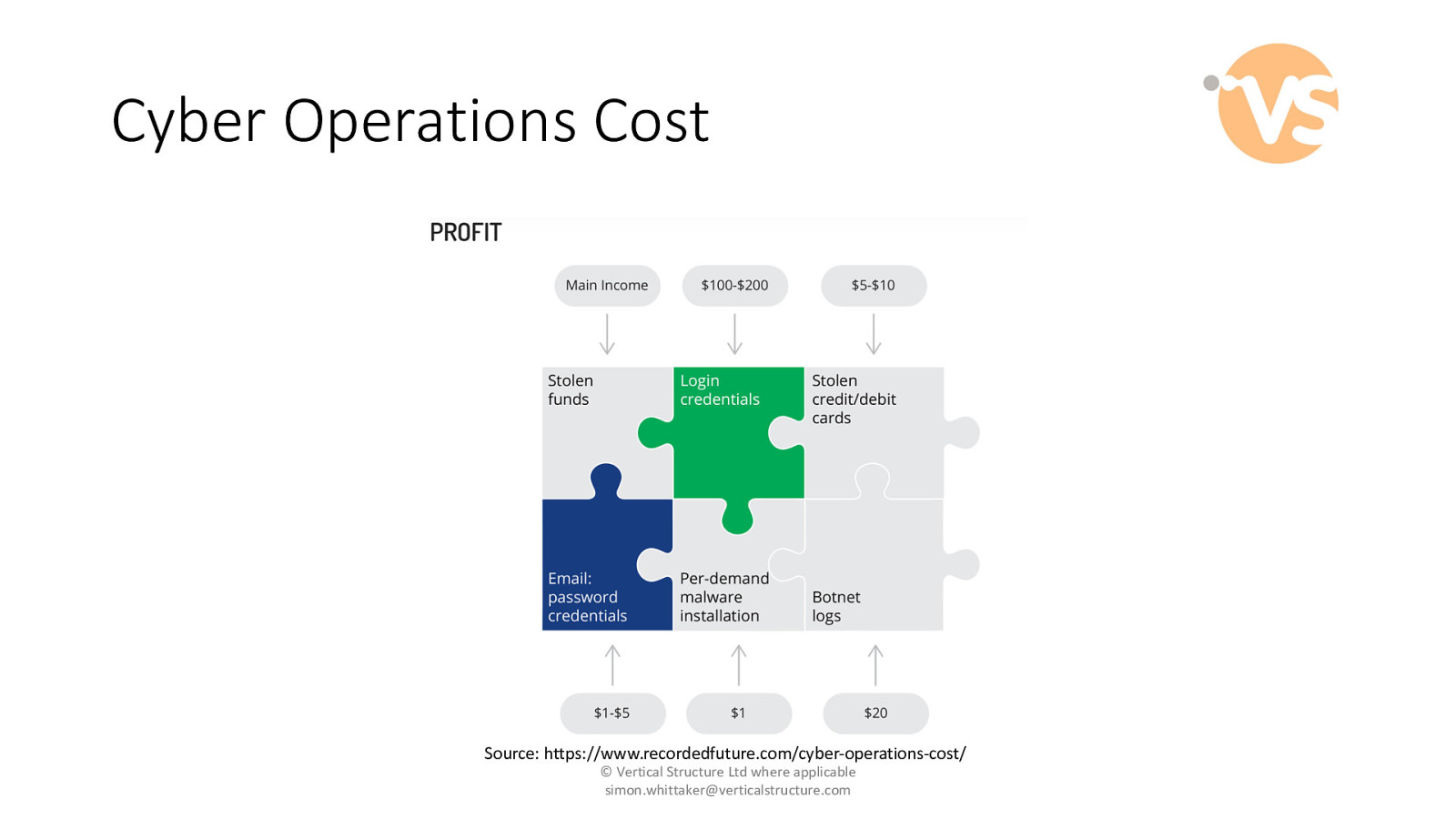
Cyber Operations Cost Source: https://www.recordedfuture.com/cyber-operations-cost/ © Vertical Structure Ltd where applicable [email protected]
Slide 7
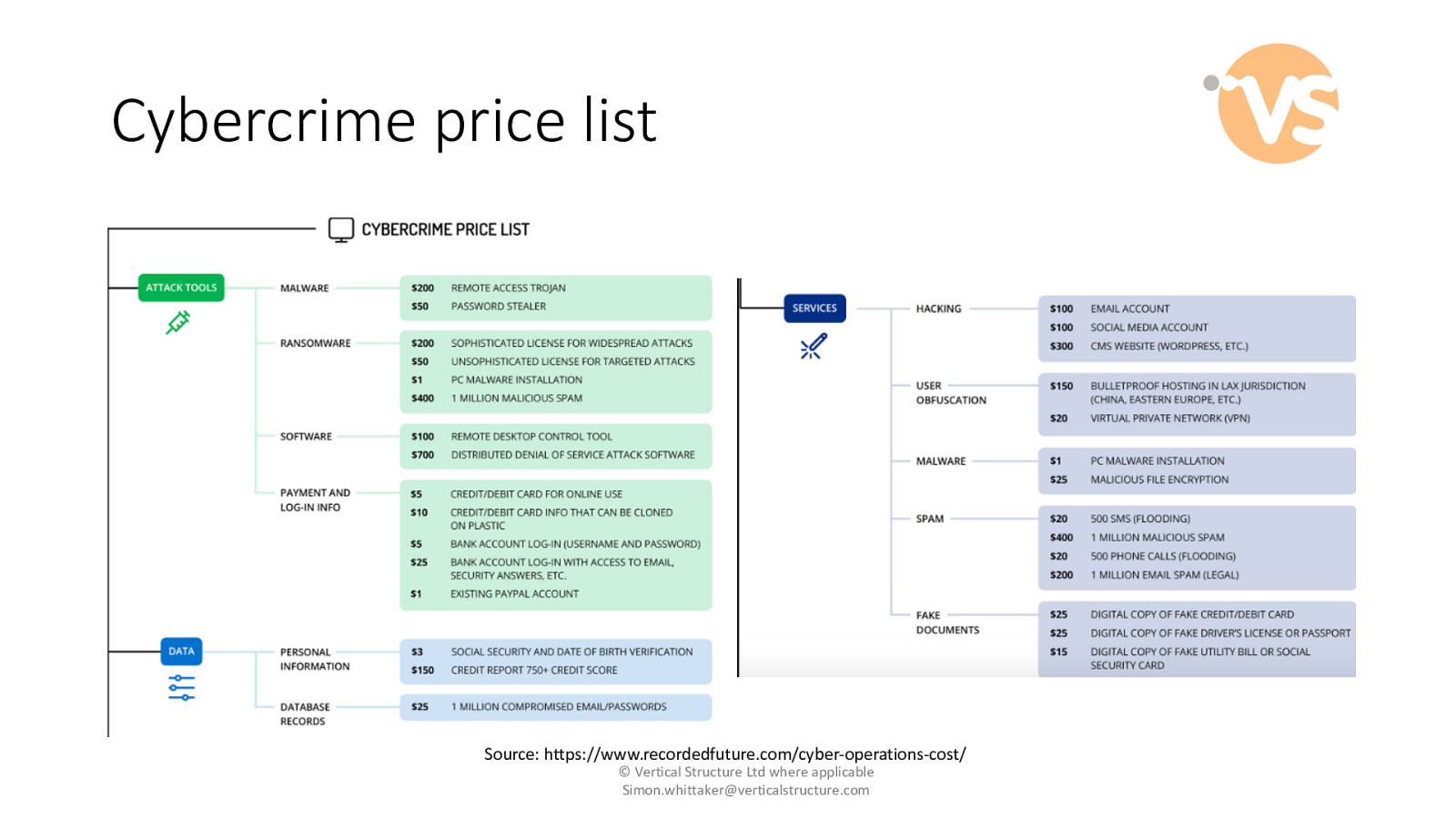
Cybercrime price list Source: https://www.recordedfuture.com/cyber-operations-cost/ © Vertical Structure Ltd where applicable [email protected]
Slide 8

”Hackers” – the stock image © Vertical Structure Ltd where applicable [email protected]
Slide 9

The reality © Vertical Structure Ltd where applicable [email protected]
Slide 10

• “It’s time to think differently about cyber risk – ditching the talk of hackers – and recognising that our businesses are being targeted by ruthless criminal entrepreneurs with business plans and extensive resources – intent on fraud, extortion or theft of hard won intellectual property.” • Paul Taylor, UK Head of Cyber Security, KPMG • http://bit.ly/takingTheOffensive © Vertical Structure Ltd where applicable [email protected]
Slide 11

© Vertical Structure Ltd where applicable [email protected]
Slide 12
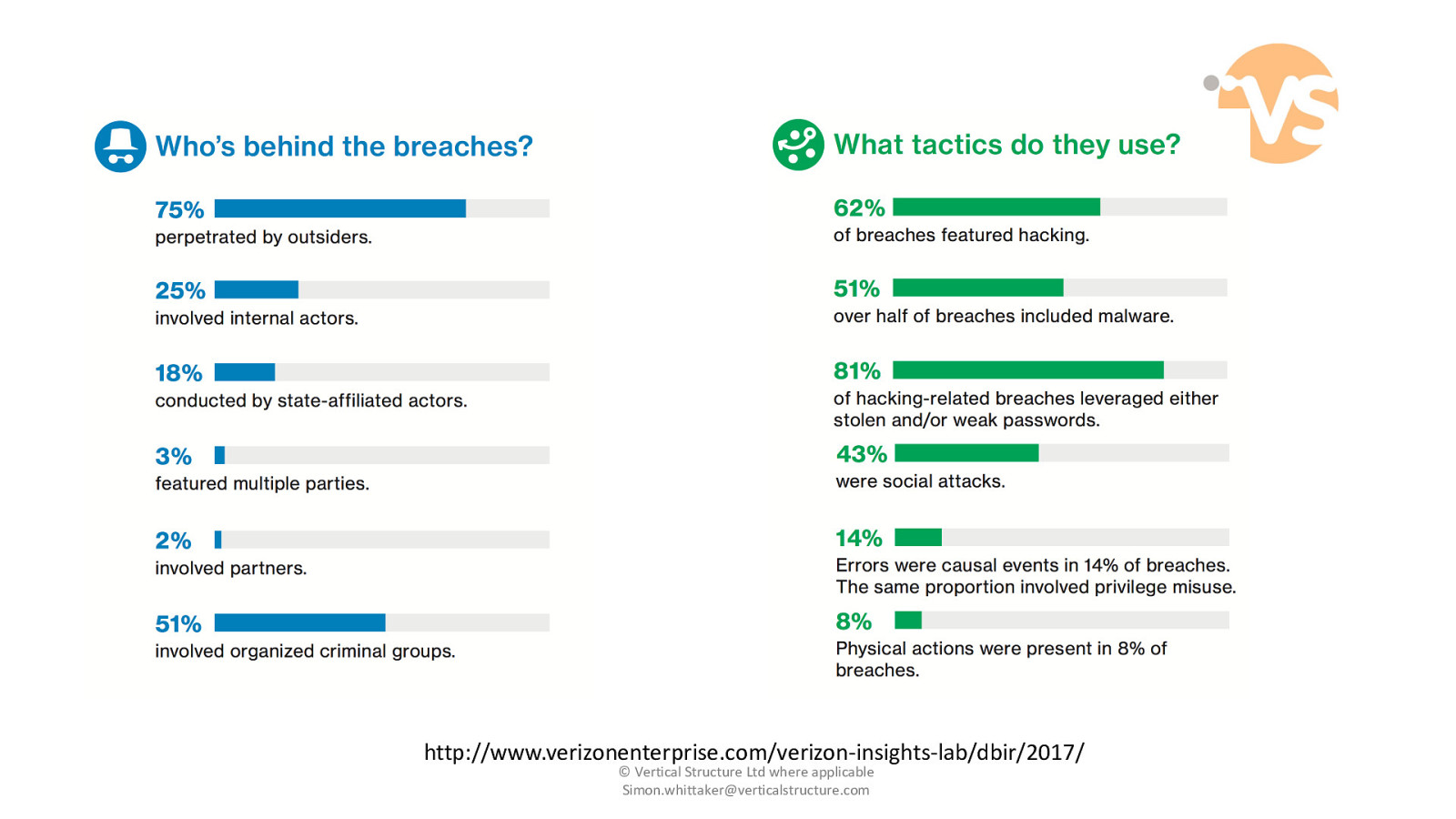
http://www.verizonenterprise.com/verizon-insights-lab/dbir/2017/ © Vertical Structure Ltd where applicable [email protected]
Slide 13
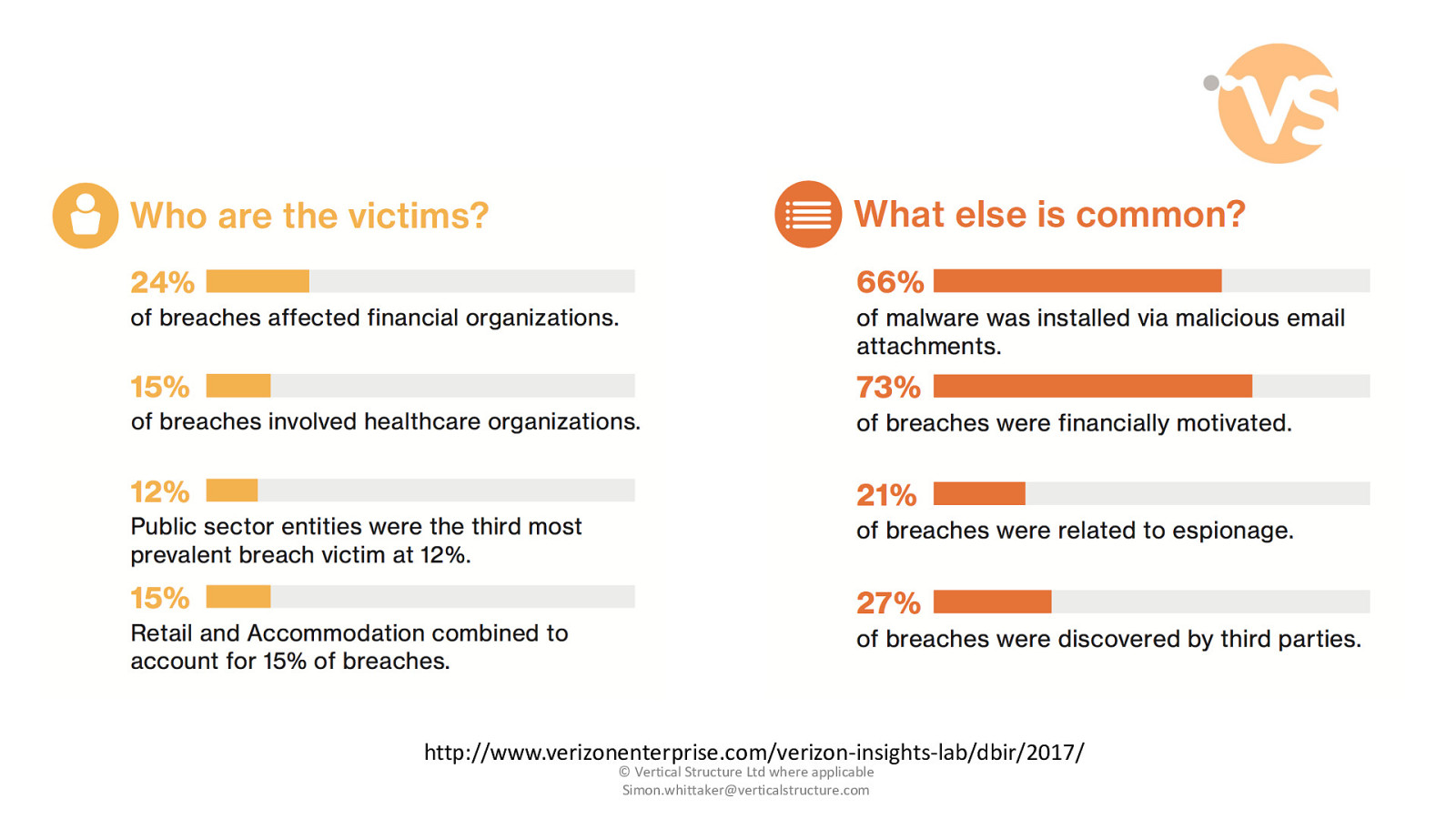
http://www.verizonenterprise.com/verizon-insights-lab/dbir/2017/ © Vertical Structure Ltd where applicable [email protected]
Slide 14
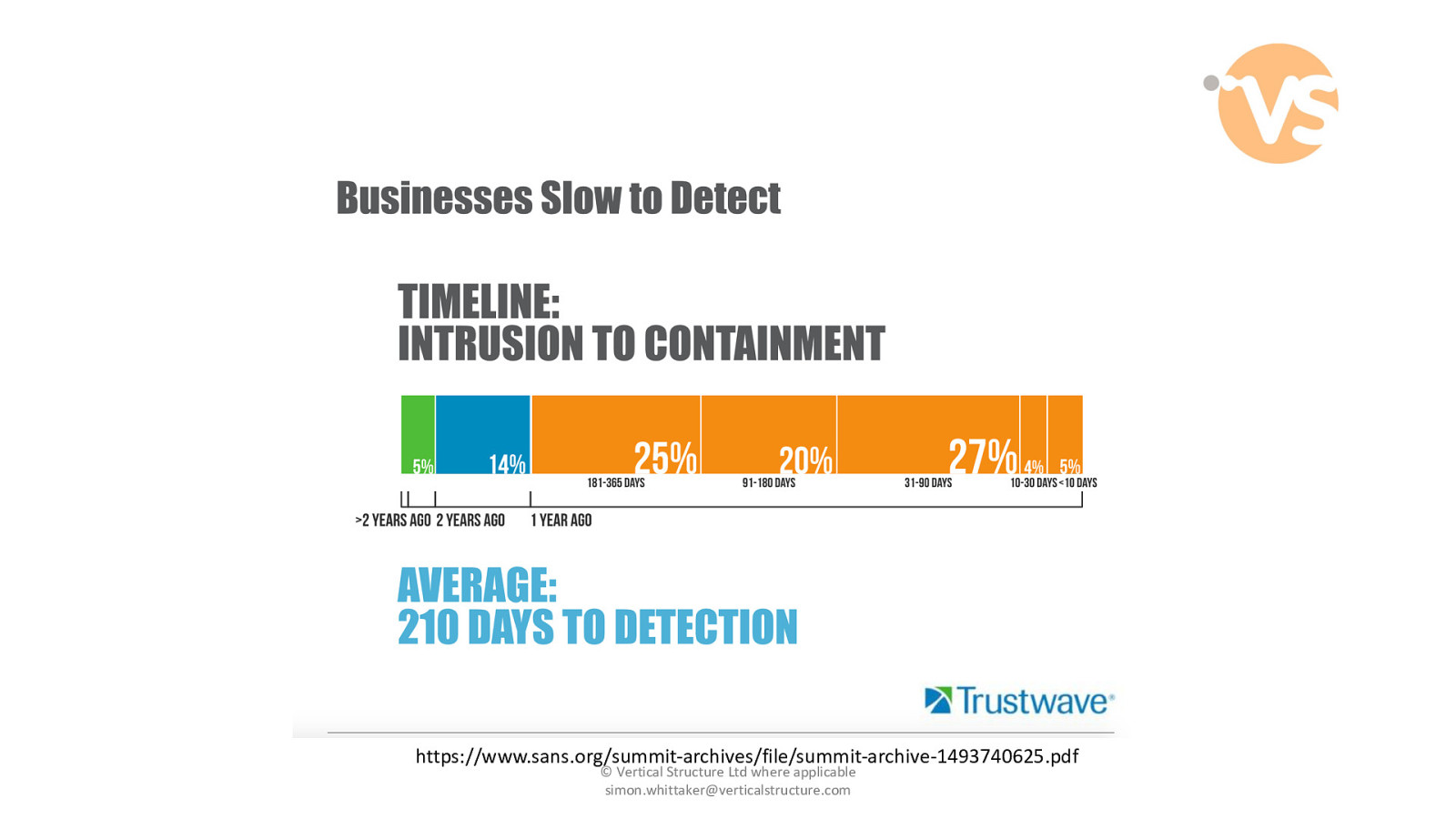
https://www.sans.org/summit-archives/file/summit-archive-1493740625.pdf © Vertical Structure Ltd where applicable [email protected]
Slide 15
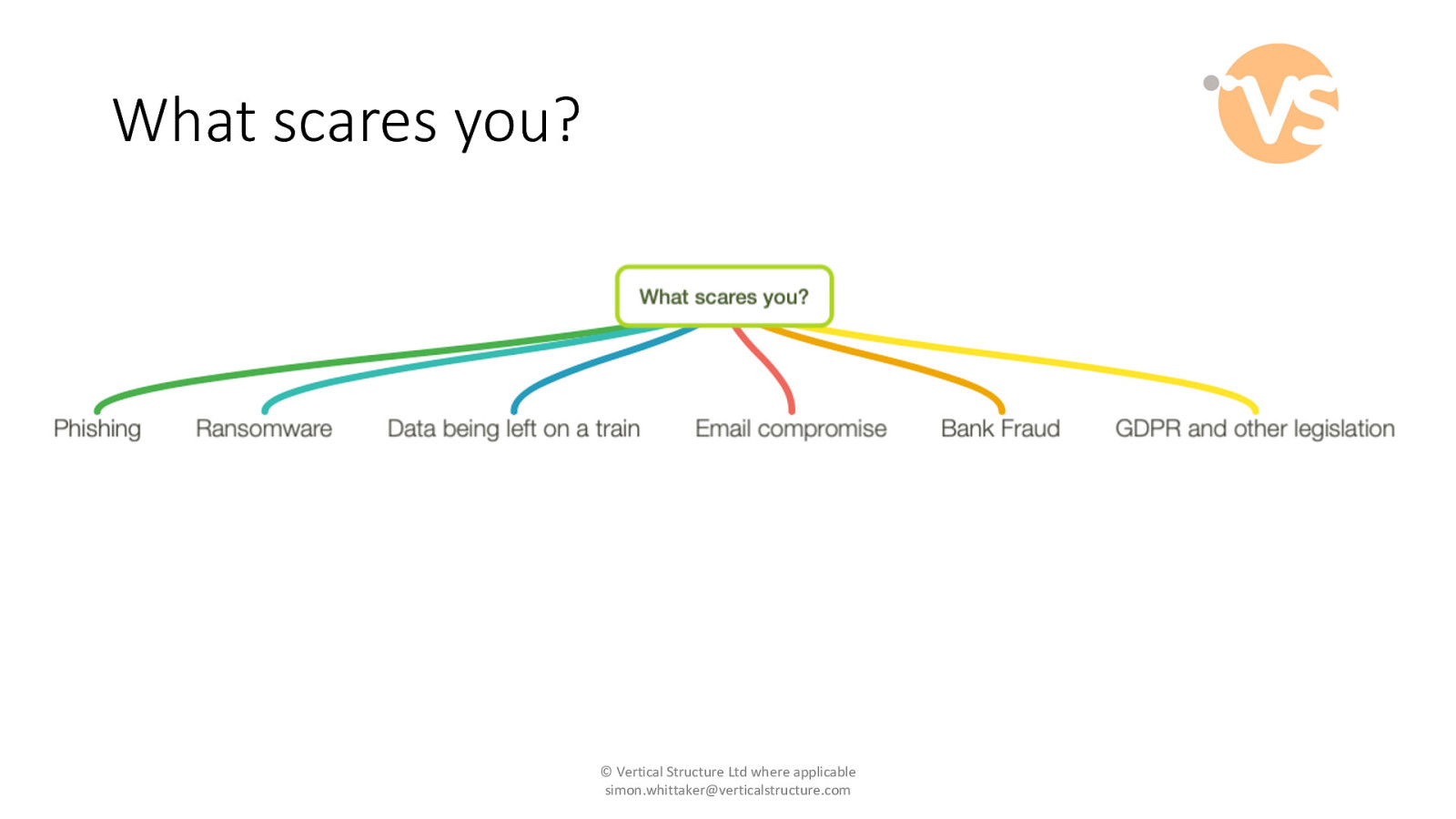
What scares you? © Vertical Structure Ltd where applicable [email protected]
Slide 16
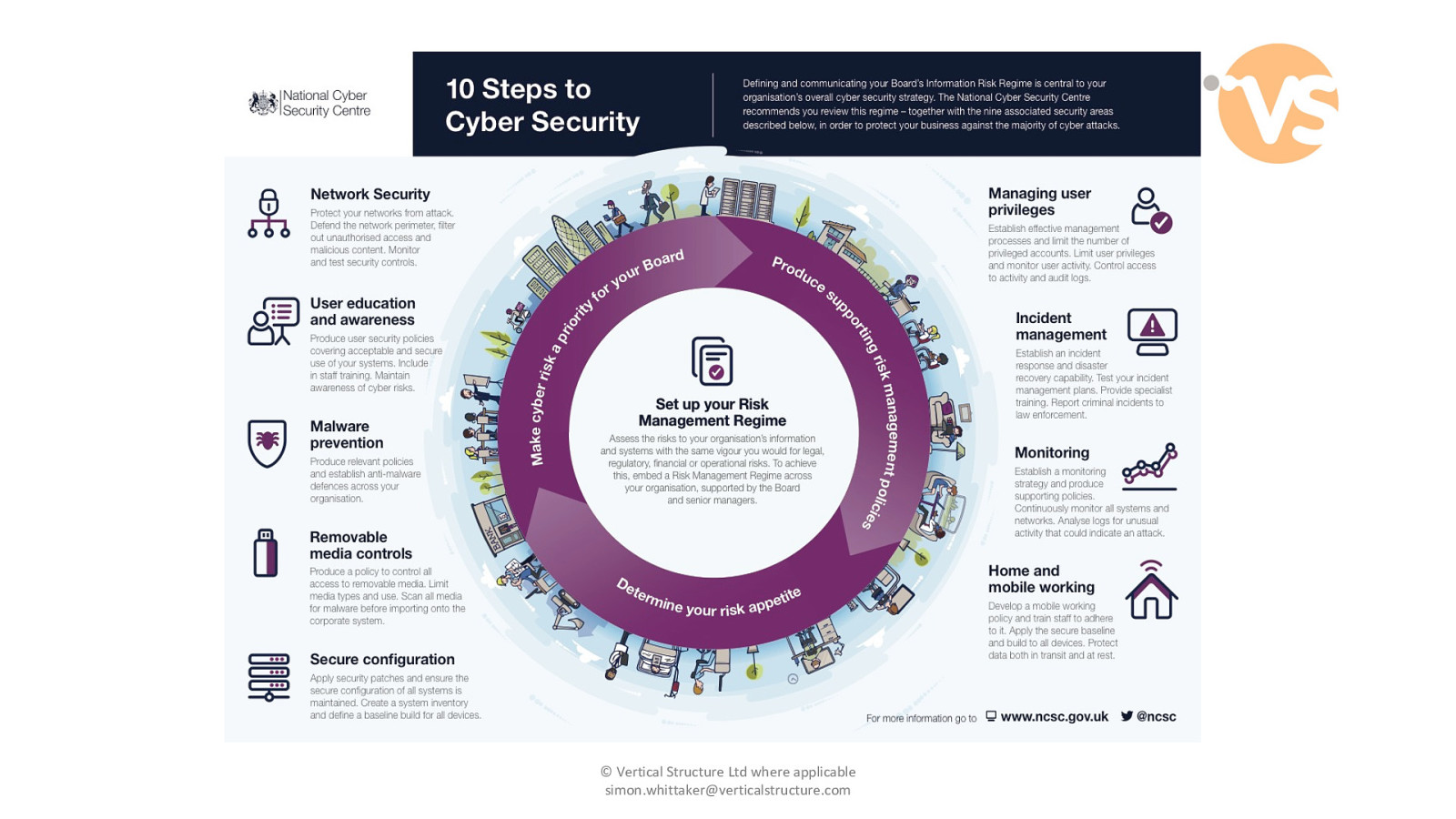
© Vertical Structure Ltd where applicable [email protected]
Slide 17

Risk Management Regime © Vertical Structure Ltd where applicable [email protected]
Slide 18

Network Security © Vertical Structure Ltd where applicable [email protected]
Slide 19

User Education and Awareness © Vertical Structure Ltd where applicable [email protected]
Slide 20

Malware prevention © Vertical Structure Ltd where applicable [email protected]
Slide 21

Removable Media Controls © Vertical Structure Ltd where applicable [email protected]
Slide 22

Secure Configuration © Vertical Structure Ltd where applicable [email protected]
Slide 23
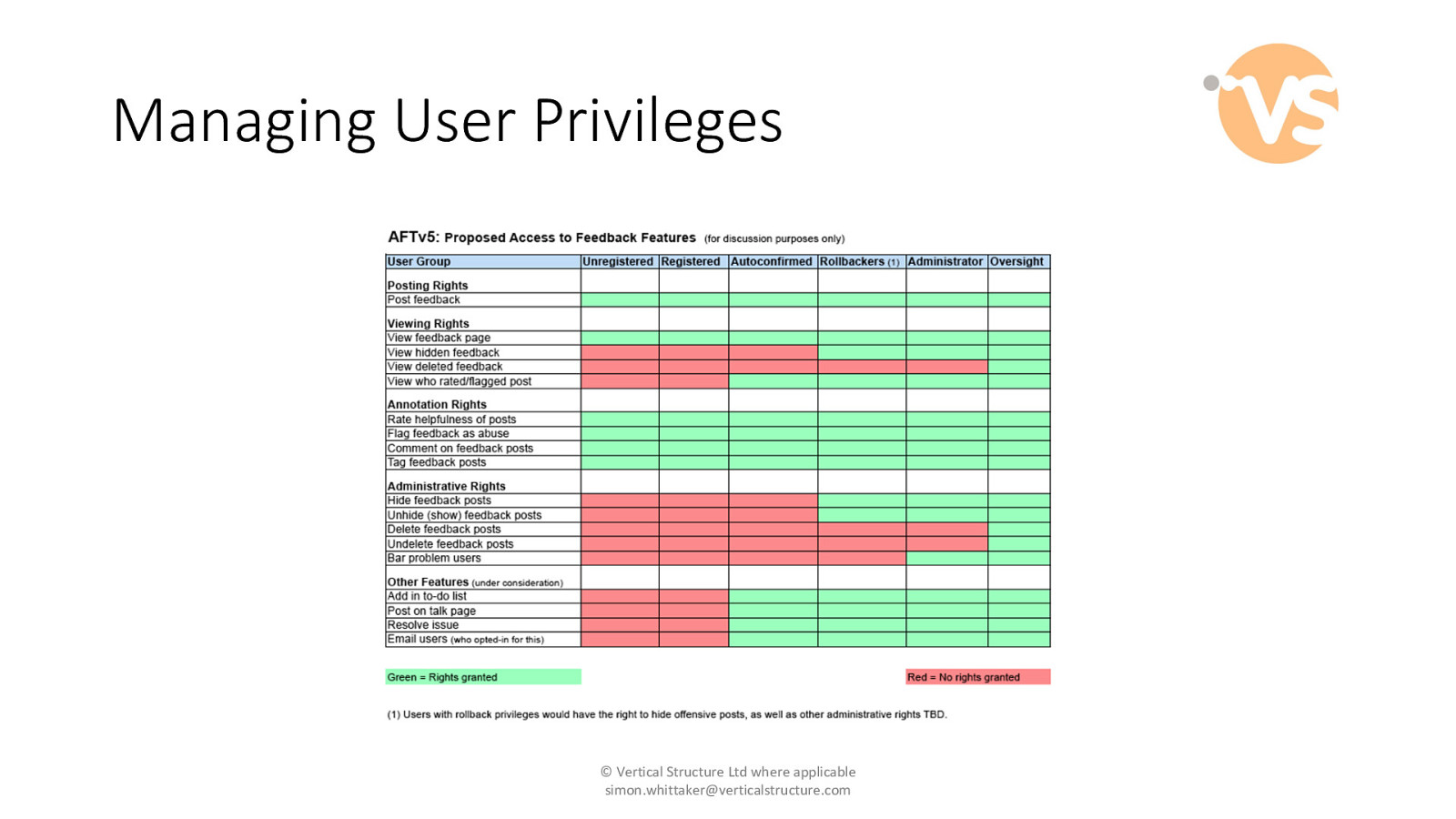
Managing User Privileges © Vertical Structure Ltd where applicable [email protected]
Slide 24

Incident Management © Vertical Structure Ltd where applicable [email protected]
Slide 25

Monitoring © Vertical Structure Ltd where applicable [email protected]
Slide 26

Home and Mobile Working © Vertical Structure Ltd where applicable [email protected]
Slide 27
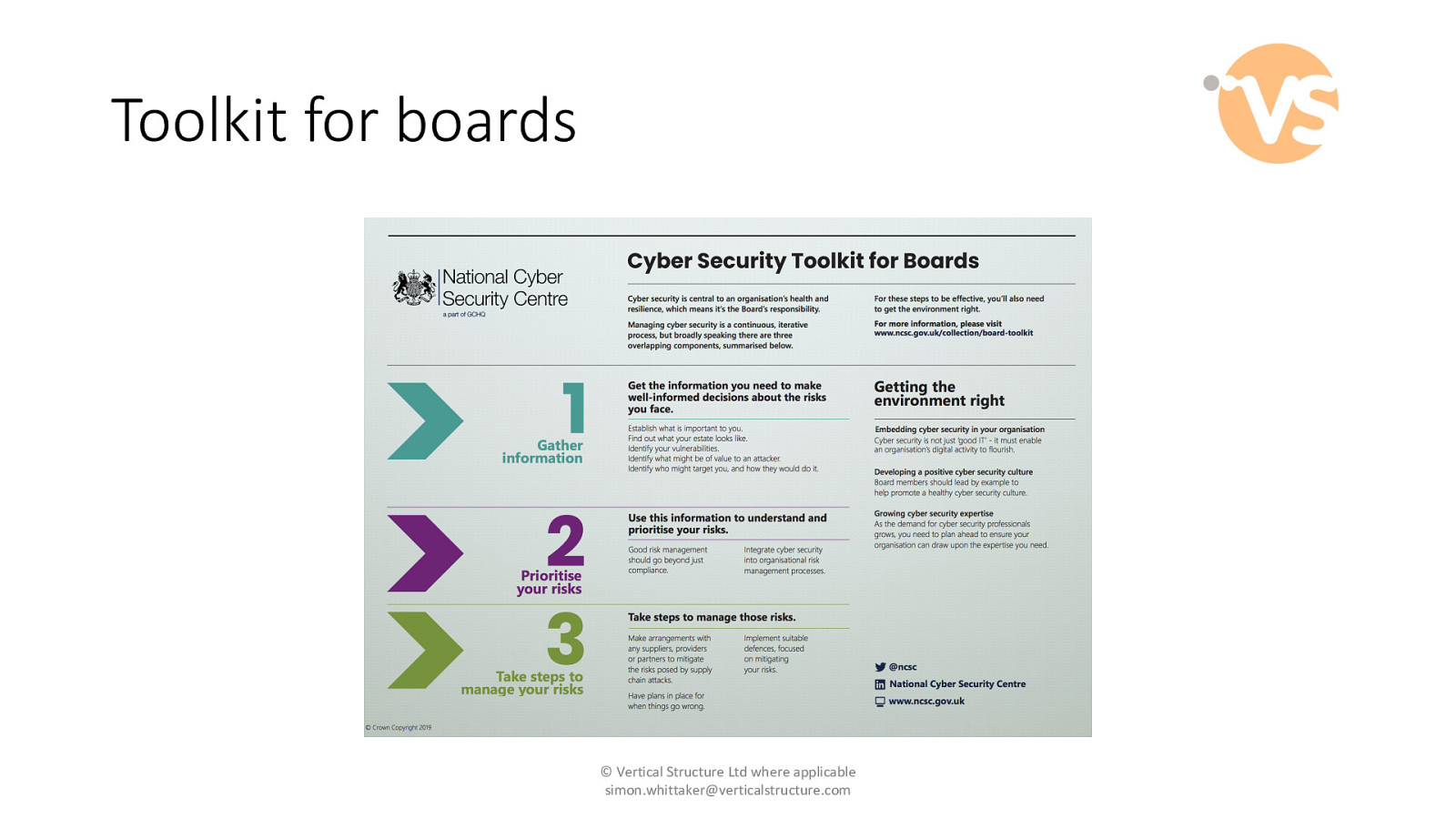
Toolkit for boards © Vertical Structure Ltd where applicable [email protected]
Slide 28

10 steps actions Network Security • Assess and test your exposure User Education • Teach your team how to respond Malware • Buy, use and update a reputable Anti-virus Removable Media Secure Configuration • Are USB sticks a benefit or hinderance? • Standardisation © Vertical Structure Ltd where applicable [email protected]
Slide 29

10 steps actions Managing Privilege Incident Management Monitoring Home and Mobile Working Risk Assessment • User addition and removal checklist • Teach your team how to respond • Reduce the time before compromise awareness • Effective policies and technology • Expand risks beyond “what if we get hacked” © Vertical Structure Ltd where applicable [email protected]
Slide 30
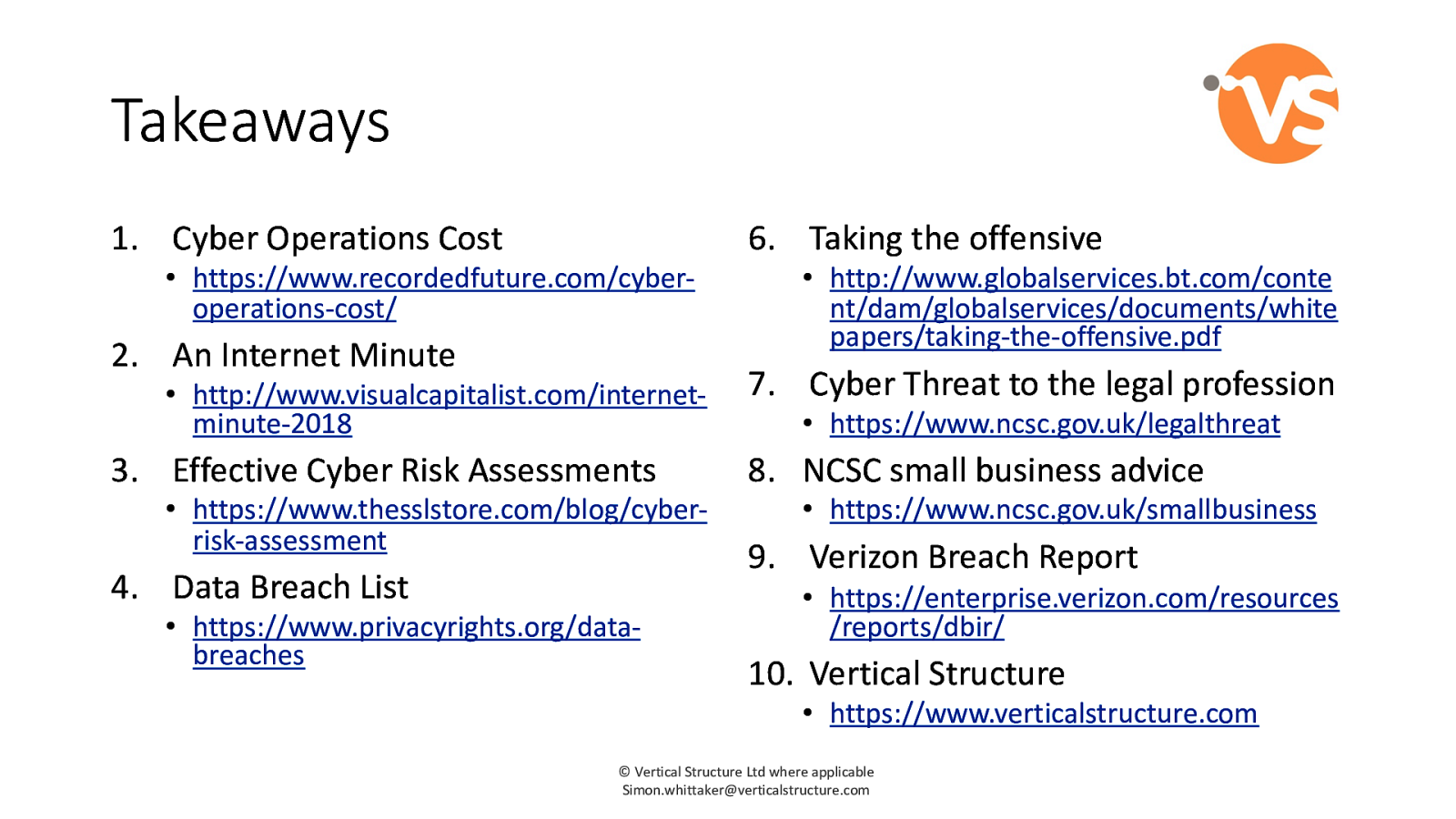
Takeaways 1. Cyber Operations Cost • https://www.recordedfuture.com/cyberoperations-cost/ 2. An Internet Minute • http://www.visualcapitalist.com/internetminute-2018 3. Effective Cyber Risk Assessments • https://www.thesslstore.com/blog/cyberrisk-assessment 4. Data Breach List • https://www.privacyrights.org/databreaches 6. Taking the offensive • http://www.globalservices.bt.com/conte nt/dam/globalservices/documents/white papers/taking-the-offensive.pdf 7. Cyber Threat to the legal profession • https://www.ncsc.gov.uk/legalthreat 8. NCSC small business advice • https://www.ncsc.gov.uk/smallbusiness 9. Verizon Breach Report • https://enterprise.verizon.com/resources /reports/dbir/ 10. Vertical Structure • https://www.verticalstructure.com © Vertical Structure Ltd where applicable [email protected]
Slide 31

Questions? [email protected] https://vsltd.co/ABNI2019