Cyber Security The Community & Voluntary Sector Simon Whittaker Cyber Security Director - Vertical Structure Ltd © Vertical Structure 2020
Slide 1

Slide 2
Prepare, Protect, Persist ® Prepare We help you and your partners to understand how to identify and resolve potential security issues at the earliest stages with hands on ‘hack yourself first’, threat modelling and GDPR compliance workshops as well as security training for non-technical colleagues. Protect Using automated and manual penetration testing techniques, we provide a comprehensive security report for your Web and mobile applications, including API testing, and networks. The report highlights potential issues and their resolutions. Persist We ensure that your organisation benefits from continual improvements in security levels through information assurance processes, auditing and certification including ISO27001:2013 and Cyber Essentials. © Vertical Structure Ltd where applicable [email protected]
Slide 3

Why is the sector being targeted? UK charities hold: • • • • Funds Personal Financial and commercial data Other information that is of interest or monetary value to a range of cyber criminals and other groups. https://www.ncsc.gov.uk/collection/charity © Vertical Structure Ltd where applicable [email protected]
Slide 4

NI Cyber exists to promote the expertise of >35 companies from NI, identifying opportunities for business and national/international collaboration, and promoting career opportunities in cyber security. © Vertical Structure Ltd where applicable [email protected]
Slide 5

© Vertical Structure Ltd where applicable [email protected]
Slide 6
Speakers Simon Whittaker – Cyber Security Director - Vertical Structure The majority of my work involves working with companies to perform penetration & security testing, test and improve secure coding practices and provide security consultancy to companies that are keen to improve their processes & procedures. [email protected] © Vertical Structure Ltd where applicable [email protected]
Slide 7

Why is the sector being targeted? Charities are subject to the same cyber vulnerabilities as other organisations and businesses that conduct financial transactions, and rely on electronically held data or information to conduct dayto-day operations. © Vertical Structure Ltd where applicable [email protected]
Slide 8

Why is the sector being targeted? The outward facing nature of charities and a culture of trust in the sector makes them particularly vulnerable to criminality.
Slide 9
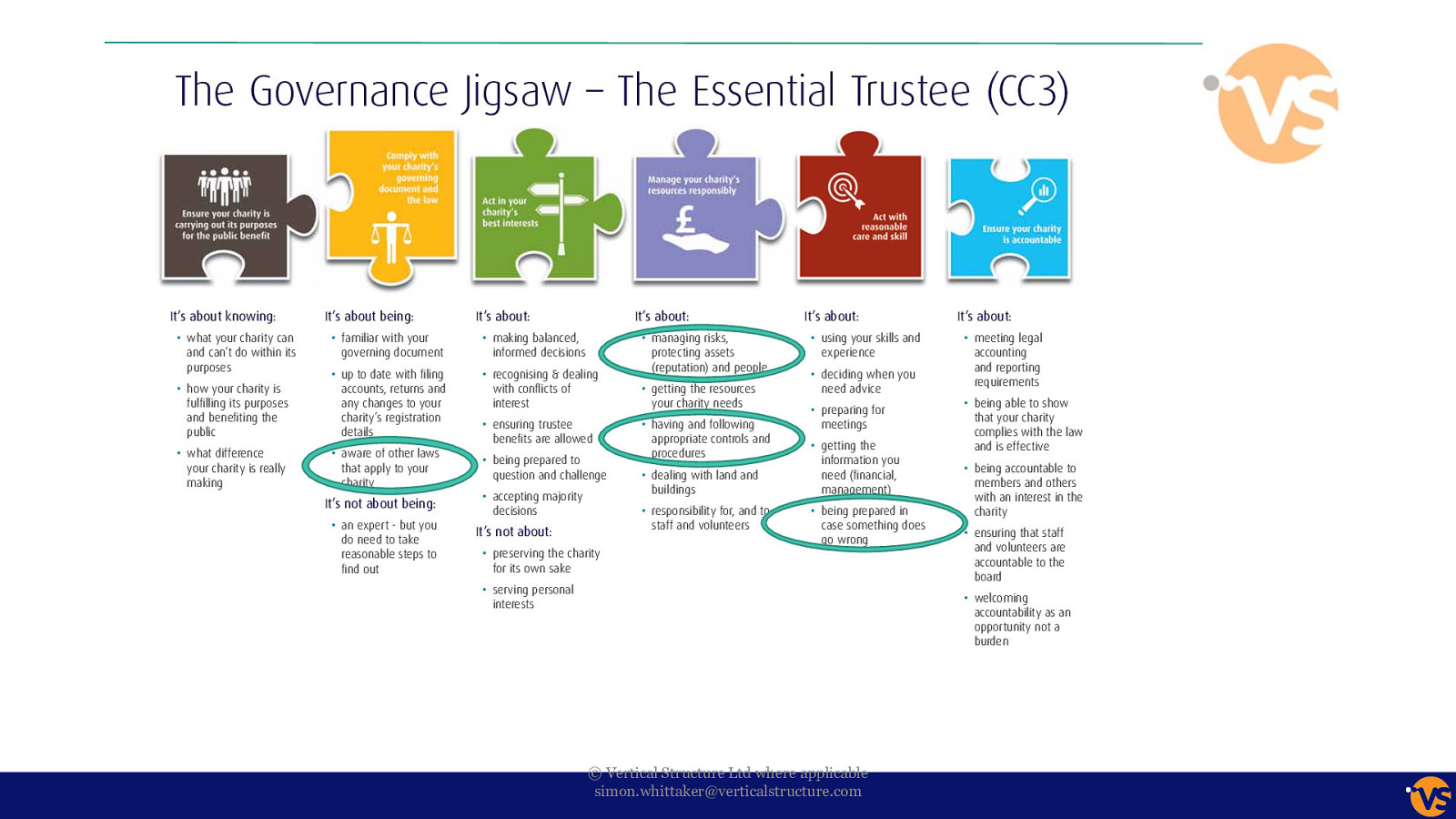
It’s about knowing: It’s about being: what your charity can and can’t do within its purposes familiar with your how your charity is accounts, returns and It’s about: It’s about: informed decisions It’s about: It’s about: experience (reputation) and people requirements interest public details what difference your charity is really aware of other laws that apply to your charity It’s not about being: an expert - but you do need to take reasonable steps to your charity needs appropriate controls and procedures decisions that your charity complies with the law information you responsibility for, and to, members and others with an interest in the charity It’s not about: accountable to the board for its own sake interests accountability as an opportunity not a burden © Vertical Structure Ltd where applicable [email protected]
Slide 10

Some Findings • UK charities hold funds, personal, financial and commercial data and other information that is of interest or monetary value to a range of cyber criminals and other groups. • The type and amount of information held varies according an individual charity’s size, objectives, structure and contacts. • Charities are subject to the same cyber vulnerabilities as other organisations and businesses that conduct financial transactions, and rely on electronically held data or information to conduct day-to-day operations. • Thirty charities interviewed for a recent government-commissioned report had collectively experienced a range of cyber breaches in the last two years including viruses, phishing emails, ransomware attacks, identity theft, website takedowns and variants of online financial fraud. • The breaches resulted in loss of funds, data and website control. Although based on a very small dataset, the findings suggest that malicious cyber activity against the charity sector is varied and enduring. https://www.ncsc.gov.uk/files/Cyber%20threat%20assessment%20-%20UK%20charity%20sector.pdf © Vertical Structure Ltd where applicable [email protected]
Slide 11

© Vertical Structure Ltd where applicable [email protected]
Slide 12
The Assessment https://www.ncsc.gov.uk/files/Cyber%20threat%20assessment%20-%20UK%20charity%20sector.pdf © Vertical Structure Ltd where applicable [email protected]
Slide 13

Where are we? © Vertical Structure Ltd where applicable [email protected]
Slide 14
Advice from the experts https://www.ncsc.gov.uk/guidance/home-working © Vertical Structure Ltd where applicable [email protected]
Slide 15

Passwords • Set strong and long passwords for your users • 2FA wherever possible • Consider admin users separately © Vertical Structure Ltd where applicable [email protected]
Slide 16

Your team may be confused • Make software easily accessible • Write howto guides for everything • What hardware should they use? • Microsoft Tech Support Calls © Vertical Structure Ltd where applicable [email protected]
Slide 17

Don’t leave the doors unlocked • Secure your cloud • Secure your office • Secure your connectivity © Vertical Structure Ltd where applicable [email protected]
Slide 18

Devices • Bring Your Own? • Encryption • Remote Wipe • Loss of Control of data • Anti-Malware © Vertical Structure Ltd where applicable [email protected]
Slide 19
Devices • Free Wifi usage • USB drives • Backups • Software updates © Vertical Structure Ltd where applicable [email protected]
Slide 20
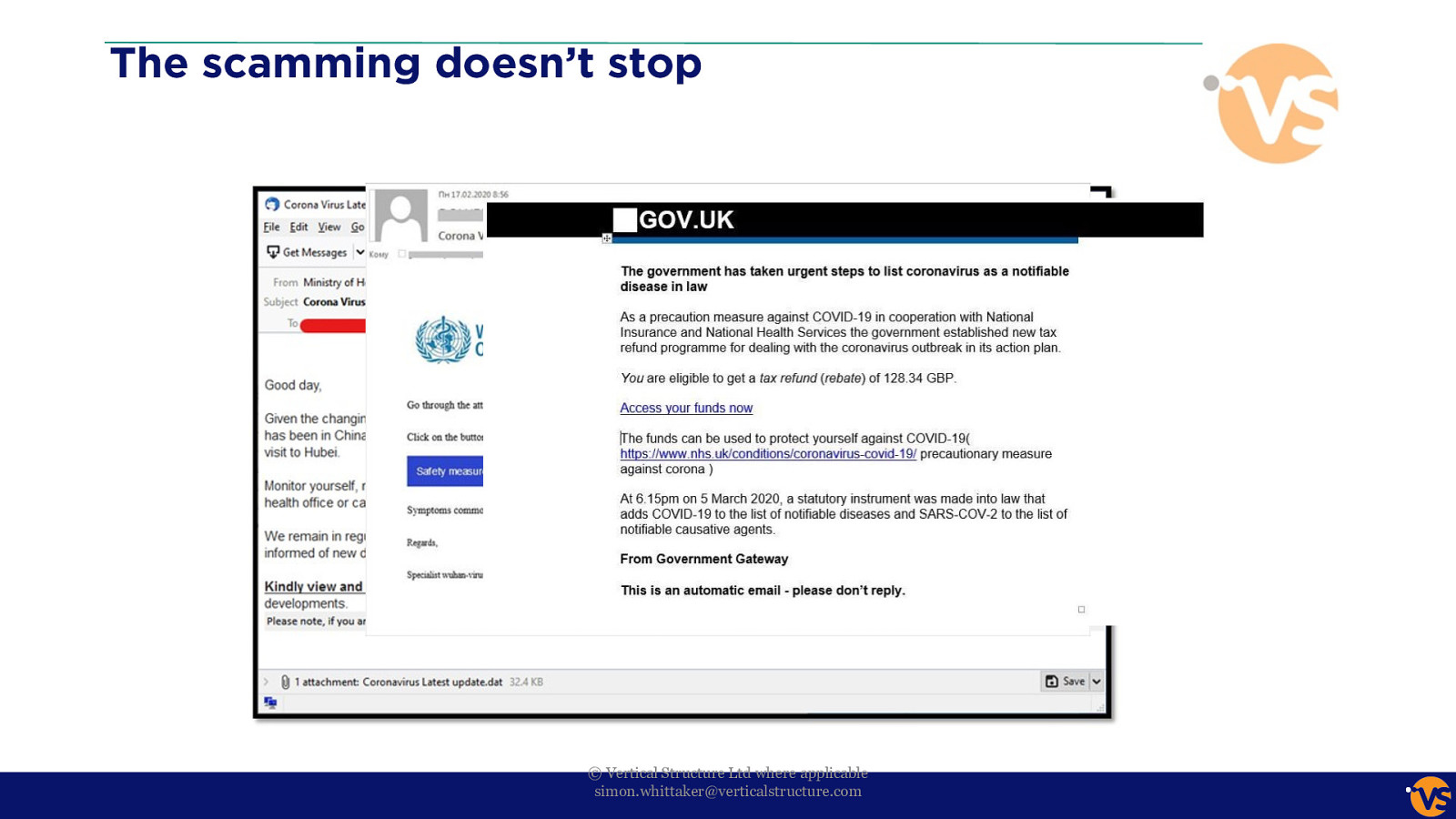
The scamming doesn’t stop © Vertical Structure Ltd where applicable [email protected]
Slide 21

Provide Training & Guidance • NCSC training for all • Practice your incident response before it happens © Vertical Structure Ltd where applicable [email protected]
Slide 22

Passwords © Vertical Structure Ltd where applicable [email protected]
Slide 23

Have you been pwned? www.haveibeenpwned.com © Vertical Structure Ltd where applicable [email protected]
Slide 24
Password Policies Users are generally told to remember passwords, and to not share them, re-use them, or write them down. But the typical user has dozens of passwords to remember – not just yours. Regular password changing harms rather than improves security, so avoid placing this burden on users. However, users must change their passwords on indication or suspicion of compromise. Gov.uk advice on passwords https://www.ncsc.gov.uk/guidance/password-guidance-summary-how-protect-against-passwordguessing-attacks © Vertical Structure Ltd where applicable [email protected]
Slide 25
Password Guidance 1. Change all default passwords 2. Help users cope with password overload 3. Understand the limitations of user-generated passwords 4. Understand the limitations of machine-generated passwords 5. Prioritise administrator and remote user accounts 6. Use account lockout and protective monitoring 7. Don’t store passwords as plain text © Vertical Structure Ltd where applicable [email protected]
Slide 26
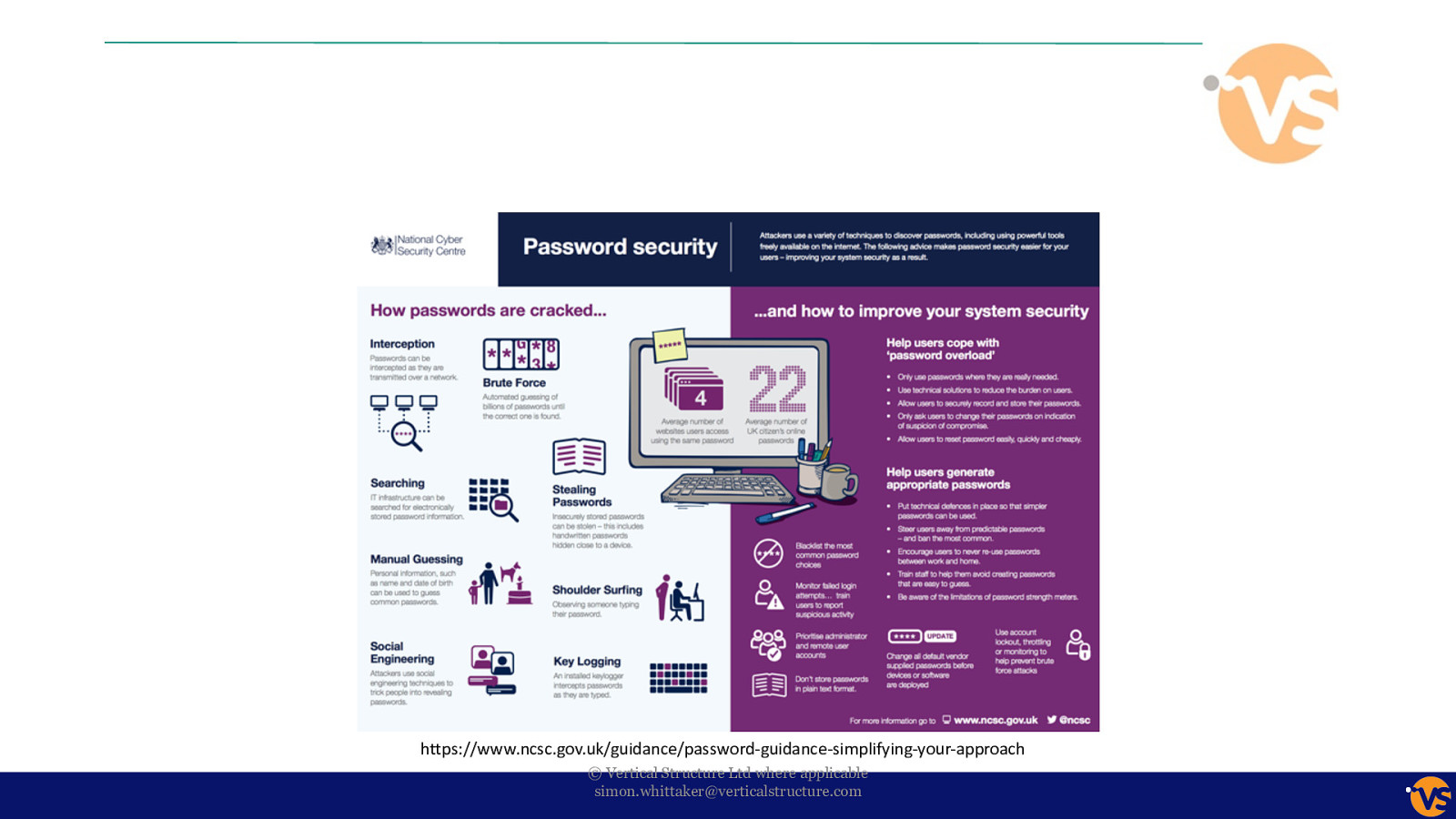
https://www.ncsc.gov.uk/guidance/password-guidance-simplifying-your-approach © Vertical Structure Ltd where applicable [email protected]
Slide 27
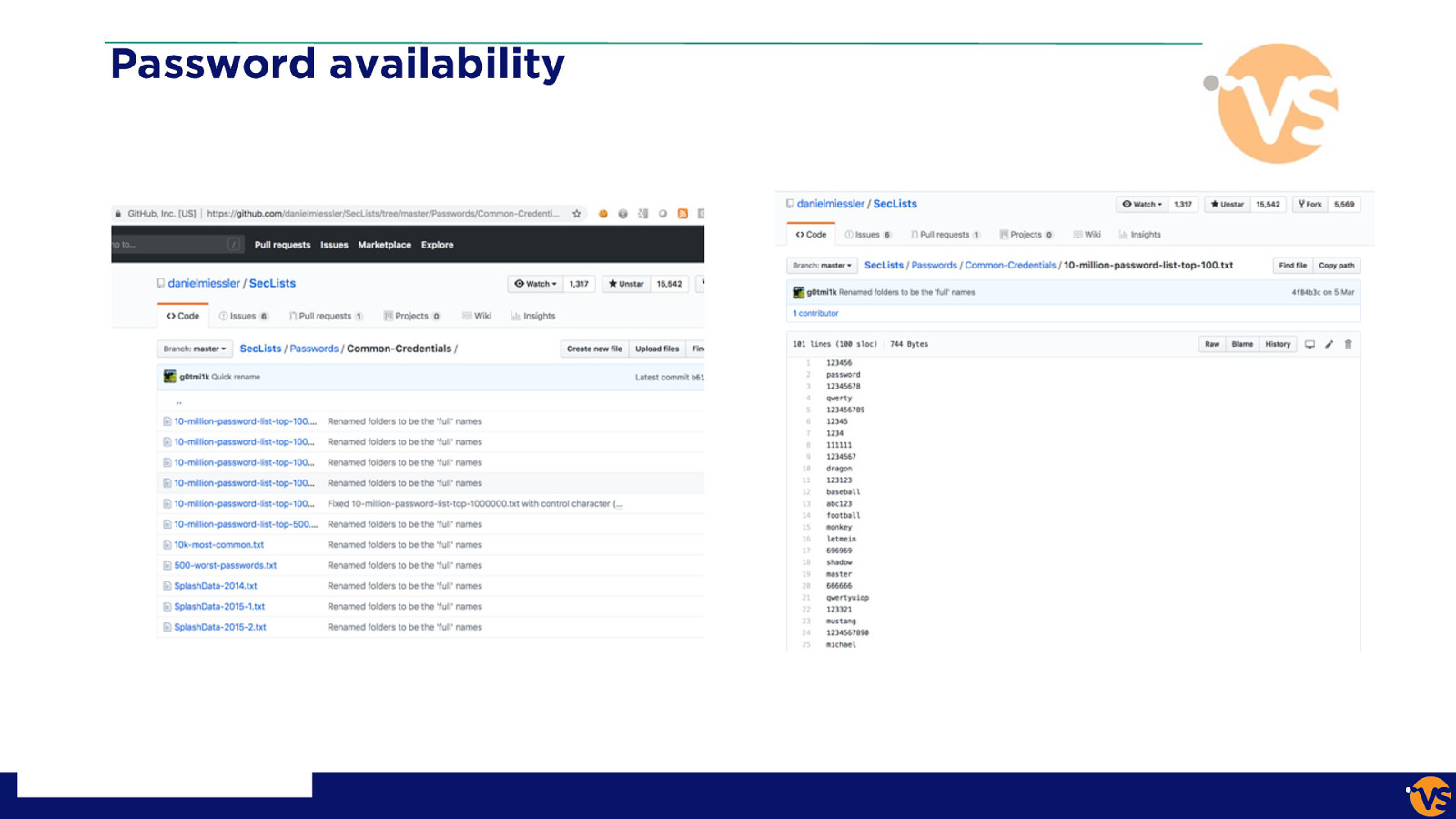
Password availability
Slide 28
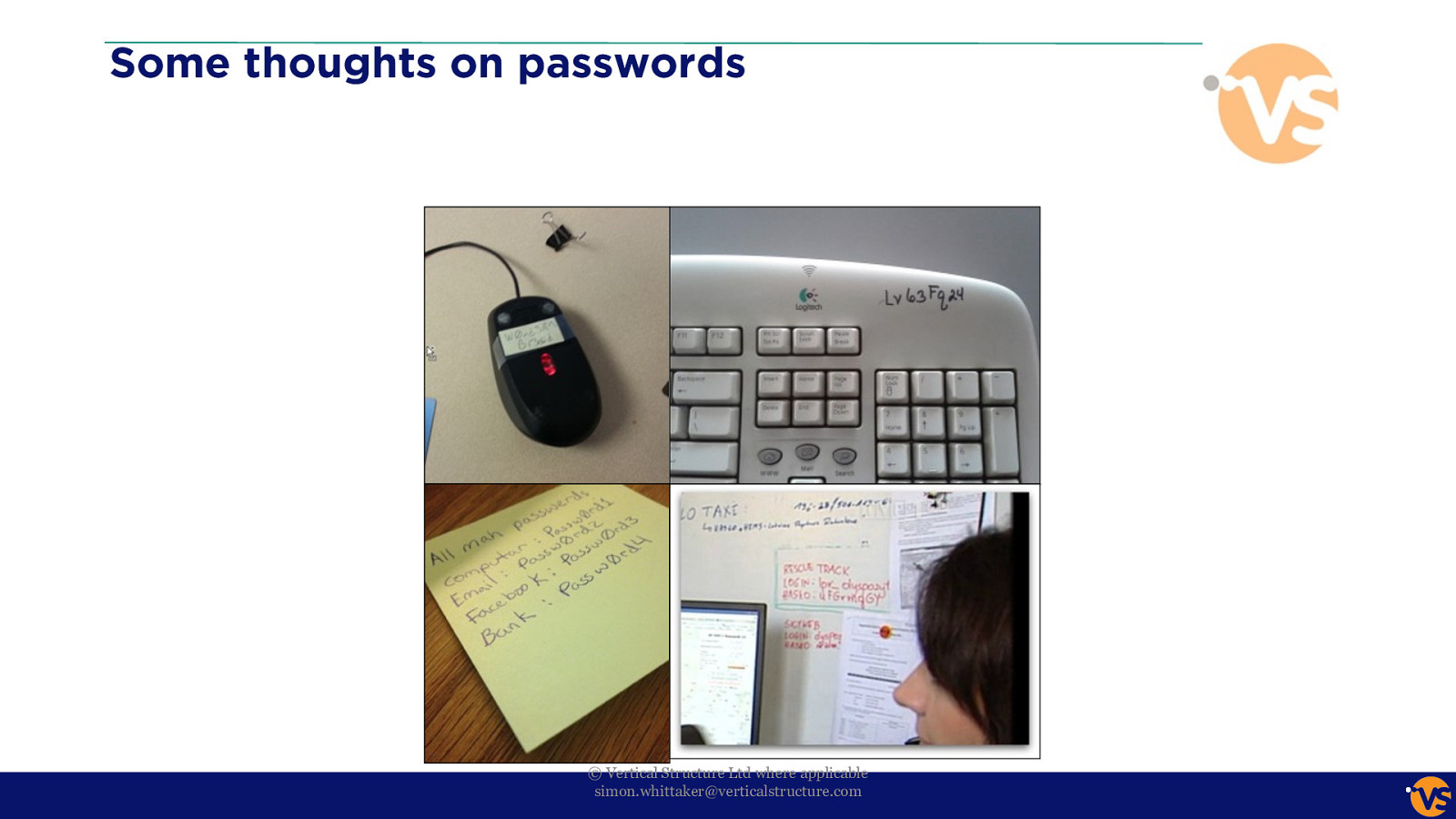
Some thoughts on passwords © Vertical Structure Ltd where applicable [email protected]
Slide 29
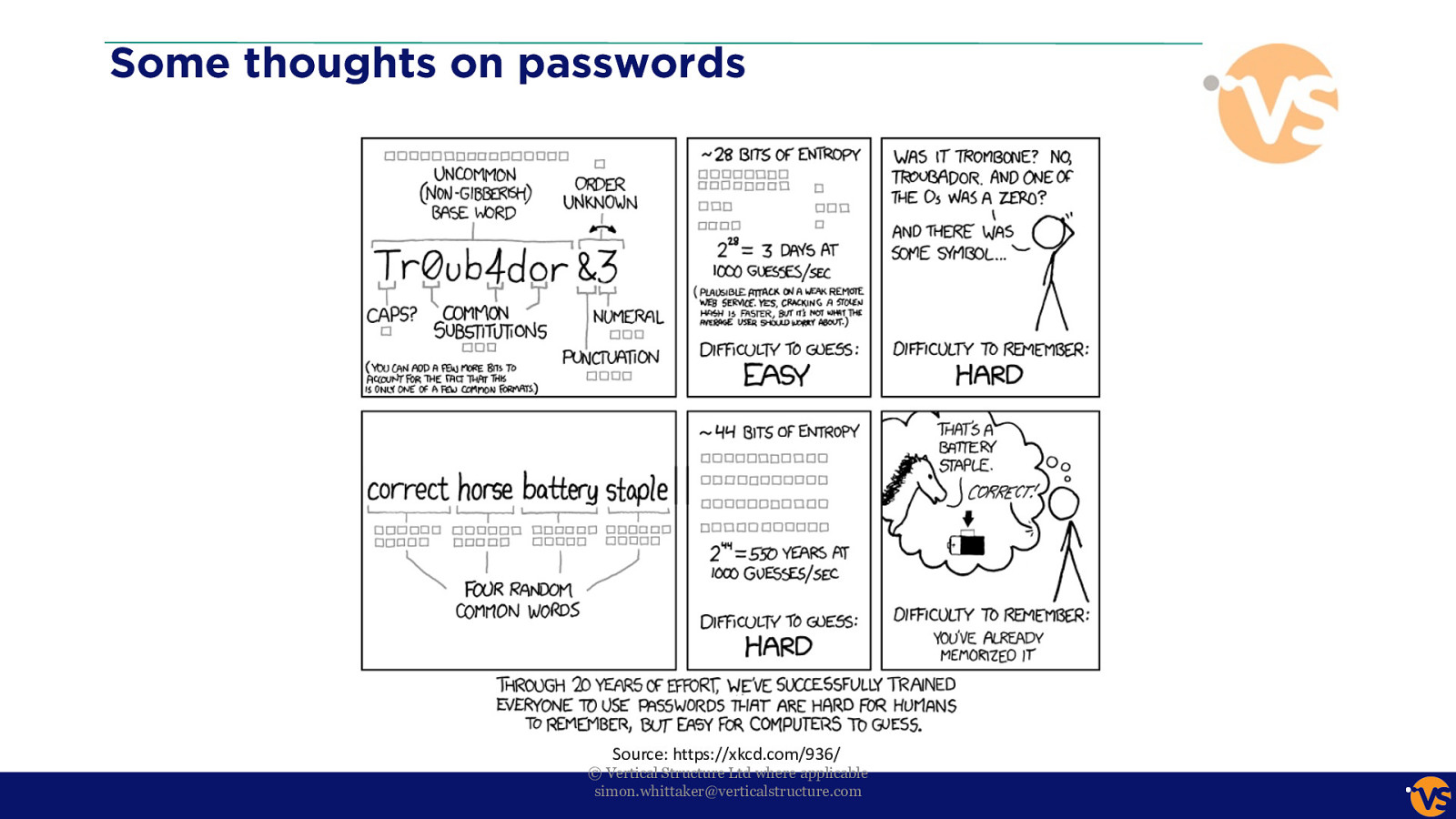
Some thoughts on passwords Source: https://xkcd.com/936/ © Vertical Structure Ltd where applicable [email protected]
Slide 30

Password Managers © Vertical Structure Ltd where applicable [email protected]
Slide 31
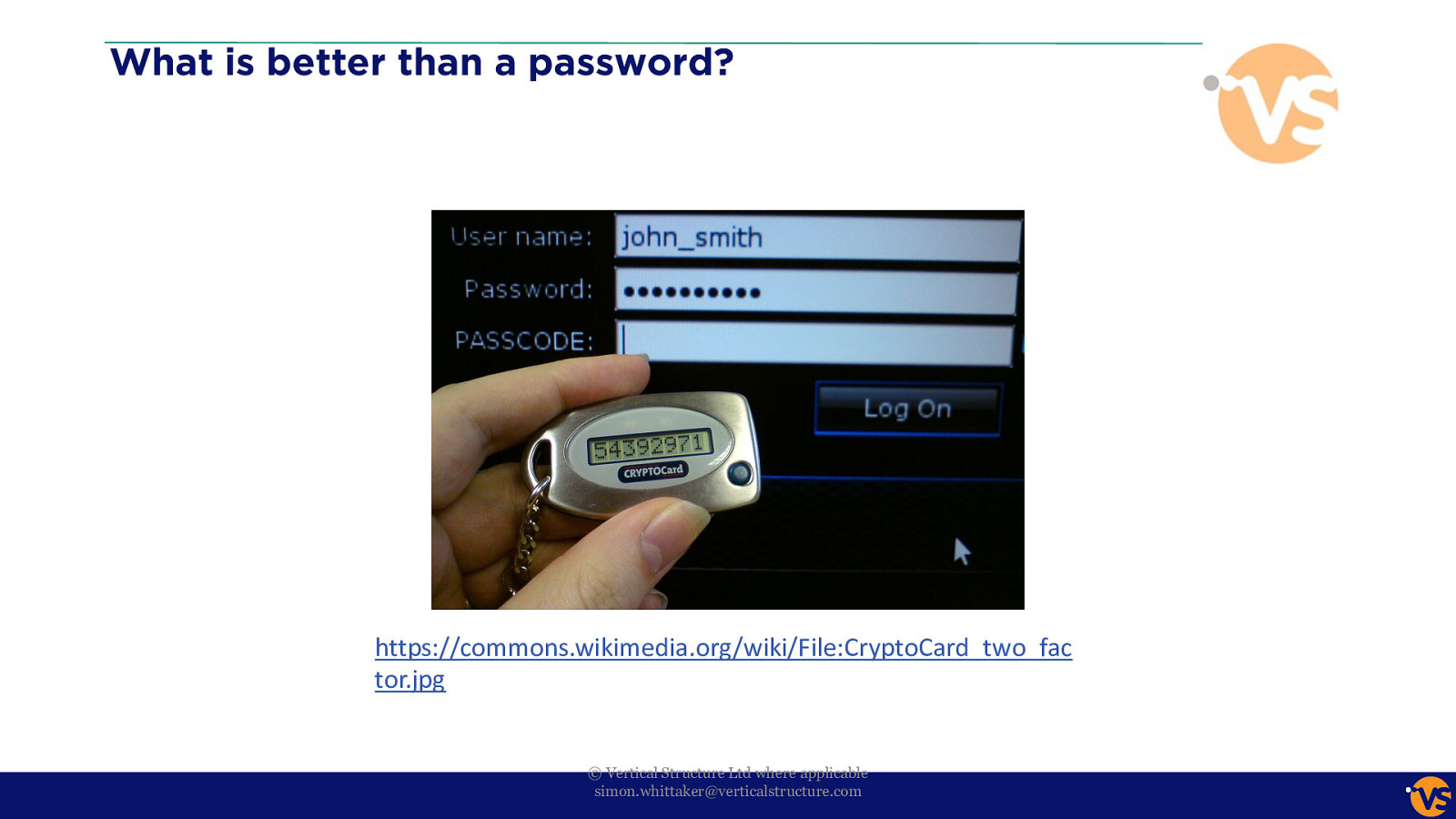
What is better than a password? https://commons.wikimedia.org/wiki/File:CryptoCard_two_fac tor.jpg © Vertical Structure Ltd where applicable [email protected]
Slide 32

Listen to your users Amy has her passwords written on a post-it note under her keyboard. Brian keeps backups of important data on his personal pen drive. Claire let David use her account – just for five minutes – while she went to make a cup of tea. People break the rules because they need to get the job done. https://www.ncsc.gov.uk/blog-post/security-breaches-communication-what-are-your-users-telling-you © Vertical Structure Ltd where applicable [email protected]
Slide 33

Backups © Vertical Structure Ltd where applicable [email protected]
Slide 34

Phishing © Vertical Structure Ltd where applicable [email protected]
Slide 35

Toolkit for boards https://www.ncsc.gov.uk/collection/board-toolkit © Vertical Structure Ltd where applicable [email protected]
Slide 36

Cyber Insurance – basic advice IASME Cyber Insurance with CyberEssentials Don’t have 2 policies! © Vertical Structure Ltd where applicable [email protected]
Slide 37

Cyber Insurance – a bit more Should cover the first-party and third-party financial and reputational costs if data or electronic systems have been lost, damaged, stolen or corrupted. Should include the cost of investigating a cybercrime, recovering data lost in a security breach and the restoration of computer systems, loss of income incurred by a business shutdown, reputation management, extortion payments demanded by hackers, and notification costs, in the case you are required to notify third parties affected. Third-party coverages (that result from claims against you) include damages and settlements, and the cost of legally defending yourself against claims of a GDPR breach. © Vertical Structure Ltd where applicable [email protected]
Slide 38

What can I do right now? Passwords • Get a password manager • Use 2 factor authentication Malware • Buy an antivirus Train your users • NCSC training • CyberEssentials © Vertical Structure Ltd where applicable [email protected]
Slide 39
Takeaways 1. NCSC Guide for Charities • https://www.ncsc.gov.uk/collection/chari ty 2. Cyber Operations Cost • https://www.recordedfuture.com/cyberoperations-cost/ 3. Data Breach List • https://www.privacyrights.org/databreaches 4. 5. NCSC small business advice • https://www.ncsc.gov.uk/smallb usiness 6. Verizon Breach Report • http://www.verizonenterprise.co m/verizon-insightslab/dbir/2017/ 7. Vertical Structure Taking the offensive • http://www.globalservices.bt.com/conten t/dam/globalservices/documents/whitep apers/taking-the-offensive.pdf • https://www.verticalstructure.co m © Vertical Structure Ltd where applicable [email protected]
Slide 40

Questions? [email protected] © Vertical Structure 2020